This article is mostly a summary of the information available here in text & video form:

In this article series Ramiro unveils the evidence of highly coordinated efforts between tech and telecom corporations, which, along with government agencies, collectively performing a massive dragnet and targeted surveillance of every citizen.
While the information is shocking, this article is not meant to incite fear, but rather consciouness to be able to understand how the tracking works, which then makes the solutions obvious.
Given that large parts of the most common operating systems (Apple's iOS & Google's Android) are proprietary, it takes well-designed independent research efforts to measure how much data collection has happened behind the scenes. Here is one such fairly recent study: Mobile Handset Privacy: Measuring The Data iOS and Android Send To Apple And Google
Study Synopsis
This study analyzed the different data captured by Android and iOS based phones. Even after the user had opted out of all data collection options, it was found that large amounts of data were sent back to Google and Apple, on average every 4.5 minutes. When the phones were unused, it was observed that the iPhone sends 52KB every 12 hours, while Google collected a staggering 1MB of data in the same time.
Apple / iOS Data Collection
Apple can use the following information to single out a device, network, or cellular plan.
Connections back to Apple servers averaged once every 264 seconds
On Every Single Connection:
- IP Address Of Phone: An inherent part of every single network connection made to a back-end server, and can be used to estimate location. Your IP will change dynamically if connecting to cell towers, allowing for the analysis of movement.
On First Start (restarting the phone from a factory reset):
- UDID: Unique device identifier, unique to the physical device.
- Hardware Serial Number: Another code that uniquely identifies the device.
- Unique Chip ID: Unique to every System-On-A-Chip (SOC). This is the chip that integrates your CPU, storage, modems, and other phone components
When a SIM Card Is Inserted:
- IMEI: (International Mobile Equipment Identity) that uniquely identifies your device across GSM networks
- Phone Number: Phone number with area code.
- IMSI: SIM Serial Number
Reglularly When The Phone Is Idle, Observed Every 2 to 3 Days:
- Local Device MAC Addresses & GPS Location: The MAC addresses (local network identifiers) of all devices connected to the same WiFi network along with GPS location if Geolocation is turned on.
- UDID
- Hardware Serial Number
- Apple Advertising ID
- IMEI
- Phone Number
- IMSI
When Interacting With Settings
- Hardware Serial Number
When Turning Location On
- All local MAC addresses (including other devices) along with GPS geolocation.
Geolocation Tracking: For Apple devices it was found that when location is enabled, not only is the current device's MAC address (which identifies the device on a local network) sent out, but also ALL the devices on the local WiFi network along with the geolocation coordinates accurate to within 10 meters, creating a device map around any iPhone without the consent of other devices.
Additional Apps & Services Collect Data:
Existing apps integrated into the operating system also are used to gather data.
For Apple this includes: iTunes, Siri, Safari, ...
Google Data Collection
Google sends all the exact information as Apple (except for the location - unless people use Google Maps or the likes).
Especially concerning with Google is the IDs sent every 10 to 20 minutes which show an interest in phones that change numbers or cellular service.
Connections to Google servers averaged once every 255 seconds.
On Every Single Connection:
- IP Address Of Phone: An inherent part of every single network connection made to a back-end server, and can be used to estimate location. Your IP will change dynamically if connecting to cell towers, allowing for the analysis of movement.
On First Start:
- RDID: Resettable Device Identifier or Ad ID, used for Google Ad Services, sent on startup, and regularly sent to Google's attestation service
- Hardware Serial Number
- Android ID
- WiFi MAC Address: The MAC address of your local network's router. (not all the devices)
- IMEI
Inserting a SIM Card:
- Hardware Serial Number
- Android ID
- IMEI
- IMSI
- Mobile Carrier Information
- Phone Number
Sent Regularly, Observed Every 10 to 20 Minutes
- Hardware Serial Number
- Mobile Carrier Information
- Phone Number
Sent Regularly, Observed Every 2 to 3 Days
- WiFi MAC Address
- IMEI
- IMSI
- User Email Address
Additional Apps & Services Collect Data:
Existing apps integrated into the operating system can be used to gather further data - For Google pre-installed system apps like Nexus, Clock, SafetyHub, Firebase, Youtube, Chrome Browser, Google Docs, all make connections to Google servers - more specifically to the Google Play Services logging endpoint.
No Way Out Of Telemetry:
No matter what settings a user chooses or whether an Apple / Google account is currently active, logs from multiple sources are aggregated and sent back regardless.
Personally Identifiable Information:
Both Google Pay and Apple Pay collect credit card information or email accounts to access their application stores, so the real identity of users and the association to their phone is pretty much guaranteed.
How can apps track device identifiers?
With the introduction of Android 10 (released in September of 2019) the OS changed the permissions for device identifiers to make it harder for apps to access them. After this update, only official Google apps or privleged system apps would be able to access the data. The following device identifiers became protected:
- IMEI (GSM) or MEID (ESN/CDMA)
- SIM Serial Number (ICCID)
- IMSI (Subscriber ID)
- Hardware Serial Number
Also in Android 10, devices started reporting a randomized MAC address to third party apps, greatly improving Android's privacy. Unfortunately 3rd party apps can still access the phone number and AndroidID to continue tracking behavior.
With GrapheneOS it is possible to generate a fake MAC address for the local WiFi network, effectivly circumventing the type of tracking that Apple is trying to do in regard to spying into local networks.
Furthermore, with GrapheneOS it is possible to simply deactivate the Network permission for any user app - that way effectively mitigating tracking by preventing any data from being sent home by the app in question.
The Cellular Service Providers
For phones the basic function used to be to make calls & texts over the cellular service, while modern phones can offer a myriad of functionalities via apps that connect over the internet. SIM cards are used to remotely connect to cell towers which provides service for not only calls & texts, but also and mobile data (GSM / 3G, LTE / 4G, 5G).
For internet based communications can users can opt for private, encrypted communication platforms, but also to route the data through an encrypted VPN service.
For calls & texts directly over the cellular service however it is a different story - users are at the mercy of intransparent tech giants, that have a bad track record in respecting their users privacy.
Let's take a closer look.
How cellular service works
When we activate and use our phones, they communicate unique identifiers to the cellular networks that allow the networks to identify us as customers, and to connect us together.
The IMEI (International Mobile Station Equipment Identity) is generated by the manufacturer and registered by your network and can be used to recognize stolen phones and ban them from the network. It can be used to uniquely identify a device - which makes it concerning that it is sent to Google and Apple.
The IMSI (International Mobile Subscriber Identity) is an identifier that exists on the SIM card which identifies the country, location, and subscriber number in the home network.
When we make calls, send texts, or generate internet traffic on our phones - these identifiers are attached to them directly or indirectly. Cellular service providers tend to hang onto this data for a long time.
What cellular data is saved, and for how long?
There is not much current information to be found concerning retention periods of customer data from, but the data we have leads to suspect that most phone companies store data for a very long time.
Sources: ACLU coordinated records request from 2011 uncovered a DoJ document which outlined the data retention policies for the top five cell phone providers.
Analysis of this document is as follows:
- Call detail records are held on average for 2 - 7 years (AT&T) or indefinitely.
- Cell phone tower usage (reveals location) is kept from a year up to indefinitely
- Text message metadata can be kept from a year to 7 years (AT&T)
- IP sessions can be kept up to one rolling year, internet traffic up to 90 days
More recent information from an independent forensic consultant in 2015 indicated that certain retention periods had been extended.
Note that we're talking about metadata - but although the content of calls and texts aren't saved (as far as we know), the metadata tying you to your contacts is available for search and subpoena from law enforcement.
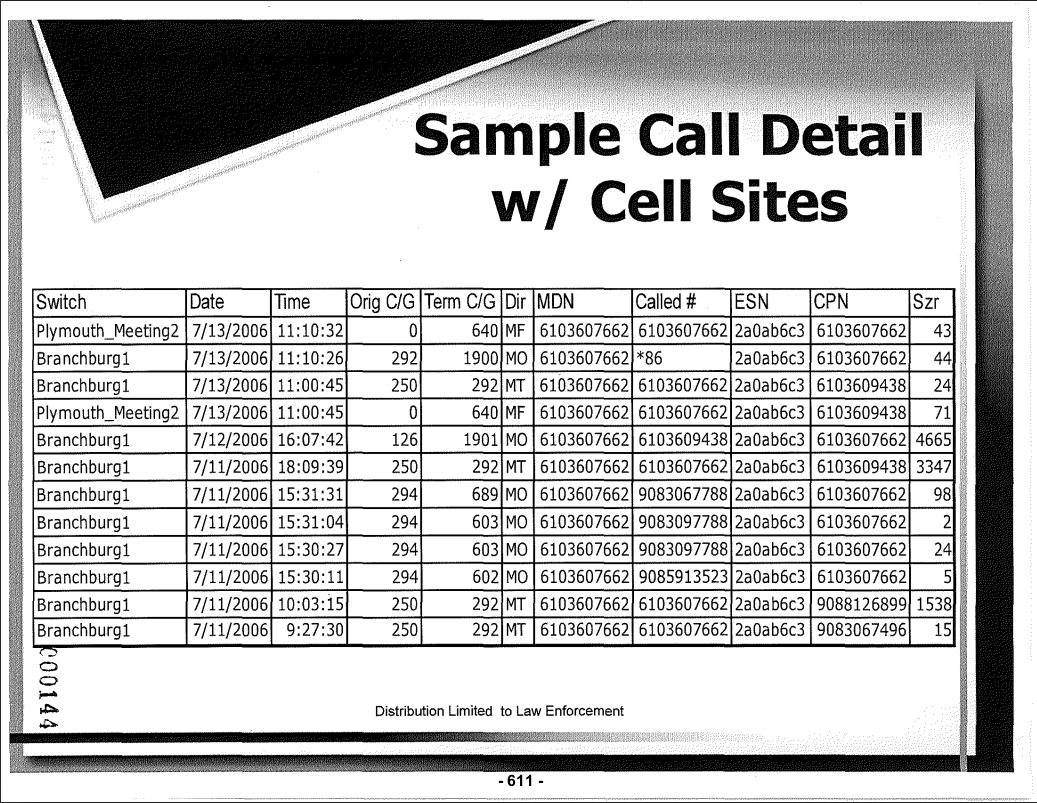
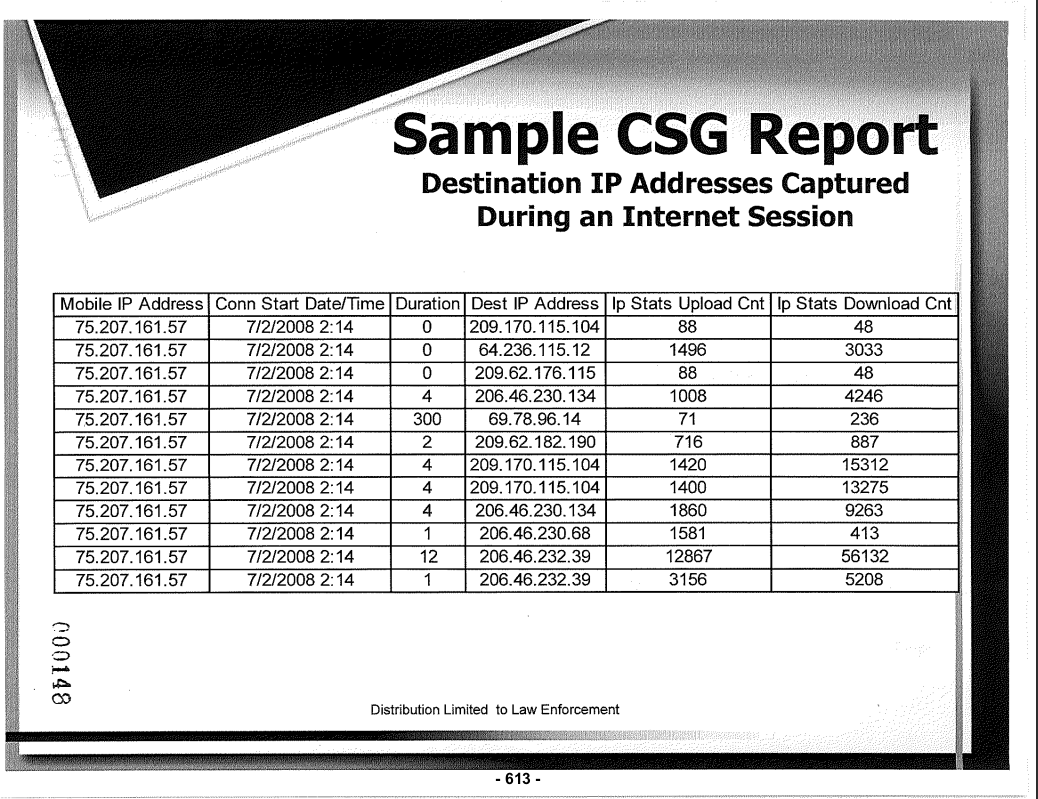
Law enforcement can request the following data: call/text/internet records, location tracking, and customer information. This allows to initiate wiretaps and pen registers (active monitoring of all calls/texts/traffic).
What are Geofence Warrants?
These are search warrants that 'compel' Google to disclose the users that were in the vicinity of a given place at a given time. How does Google have this information?
On Android phones with location history on, location data is collected in an internal Google database called Sensorvault, which agencies would use to obtain warrants. The New York Times story turned into a scandal, after innocent people were arrested, showing Sensorvault as a perfect example of the modern surveillance state we live in.
Google is not alone in its geofence capabilities - services like Apple, Lyft, Snapchat, and Uber also receive these warrants.
Administrative Warrants
With covert programs run by certain government agencies, warrants may not even be needed. One major program that was revealed to the public is DEA's Hemisphere, which was revealed in 2007. Its goal was to provide federal and local agencies near real-time search capabilities across billions of call detail records (CDRs). The program partnered with AT&T to collect CDRs across any telecom provider that used an AT&T switch. Through this program, 4 billion new call records were collected every day - and CDR data going back to 1987 was also integrated its database.
This project was particularly effective at connecting multiple phone lines with individuals, even if not registered in their name.
- Dropped Phones: An algorithm that is used to find the new number of a person who has gone dark on their existing line
- Additional Phones: A program that can be determine whether a target has additional phones
- International Phones: A program that provides records for international or roaming numbers
Hemisphere shows us that deep state surveillance programs can be massive in scale, and completely self-contained. Programs like these go to incredible lengths to hide themselves from the public. They also show a high level of technical sophistication that makes being anonymous very difficult, even with burner phones. Our knowledge of these programs is dated and highly limited. It has been a decade, and their work likely has not stopped. Other infamous Deep State surveillance programs include FAIRVIEW, PRISM, and ECHELON.
Principles Of Cellular Responsibility
We now have a better picture of how exactly cell tracking works, and with this information we have a natural set of responsibilities as a safe mobile user.
Principles Of Cellular Responsibility
- Be aware of the telecommunications collection process - consider all phone calls and texts compromised.
- Operating without a SIM card would be the safest, using trusted WiFi networks instead. If you use a SIM card and want to disconnect your usage from your previous identity, many precautions must be taken.
Check out our article on using your phone without a SIM card here! - Use a VoIP service - this way the phone number is not directly tied to a physical SIM card. Ideally your VoIP provider doallesn't require any personal information and offers private payment options, ex. crypto or cash (we recommend using JMP.chat)
- Opt for a data-only SIM card - the biggest concerns with SIM cards are connected to the phone number & calling functionality. When data is transmitted over the internet, it allows to not only use more private, encrypted communication platforms, but also to route the data through an encrypted VPN service.
We do offer a data-only SIM card of our own - the Above SIM. - Take ownership of your phone's operating system, by using something like GrapheneOS (which the Above Phone uses), which gives you full control over apps.
- Adapt to using friendly software services & applications. Avoid logging into previous big tech accounts on new devices, at risk of deanonymizing our phone.
- Protect your internet traffic and communications. When at all possible, use a VPN service that you trust combined with encrypted communications. The Above Privacy Suite offers both of these services. Instead of making phone calls, try encrypted calling using XMPP.
Conclusion
There is no one we can call on to ensure our privacy except ourselves. The organizations listed in this article have designed the mobile ecosystem so that it's data feeds into their coffers. It takes a concerted effort and lifestyle change to remove all of the tracking from our devices and internet usage. Not everyone will be willing to go to the trouble, but those who do will be setting themselves up to operate unimpeded far into the future.
Remember, our connection is sacred.
Related links: